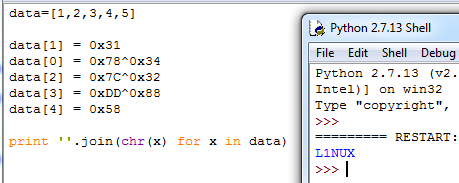
Purpose: Input the correct flag in textbox
File name: CSharp.exe
File type: Portable Executable 32 .NET Assembly
File info: Microsoft Visual Studio .NET

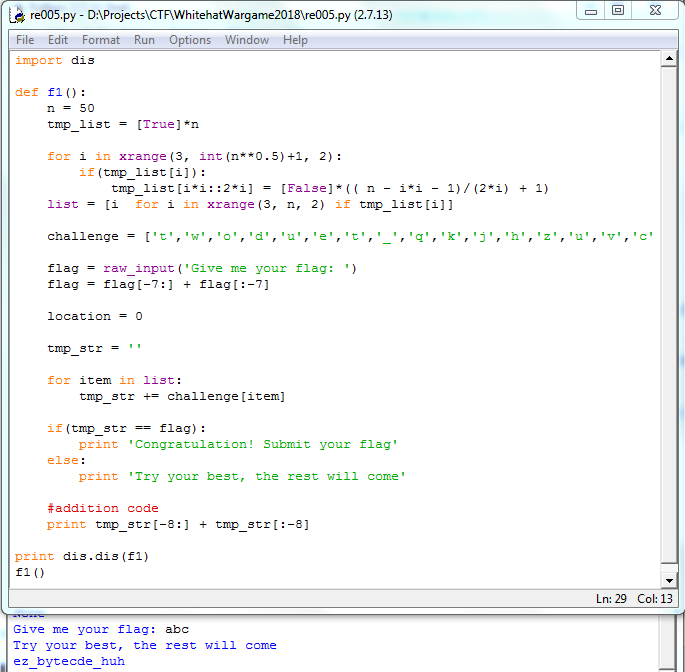
Using dnSpy to decompile the file. Go to function Main(), we can see that it has run the Form1()

Go to function btnCheck_Click(), we found that it call function MetMetMet() with input is our flag

In function MetMetMet(), the body of confirm method was created by Form1.bb

When Form1() was created, Form1.bb was loaded from function MetMett() and had some changes. Thus, the original MetMett() was changed to another function but we can’t read the changed code in Debug mode.

Set breakpoints at line 6 and line 25 to read bytes of original MetMett and changed MetMett. Find address of original in PE file and replace them with changed MetMett by HxD. Reload file in dnSpy and we can see new MetMett() 🙂
private static void MetMett(byte[] chk, byte[] bt)
{
if (bt.Length == 12)
{
chk[0] = 2;
if ((bt[0] ^ 16) != 74)
{
chk[0] = 1;
}
if ((bt[3] ^ 51) != 70)
{
chk[0] = 1;
}
if ((bt[1] ^ 17) != 87)
{
chk[0] = 1;
}
if ((bt[2] ^ 33) != 77)
{
chk[0] = 1;
}
if ((bt[11] ^ 17) != 44)
{
chk[0] = 1;
}
if ((bt[8] ^ 144) != 241)
{
chk[0] = 1;
}
if ((bt[4] ^ 68) != 29)
{
chk[0] = 1;
}
if ((bt[5] ^ 102) != 49)
{
chk[0] = 1;
}
if ((bt[9] ^ 181) != 226)
{
chk[0] = 1;
}
if ((bt[7] ^ 160) != 238)
{
chk[0] = 1;
}
if ((bt[10] ^ 238) != 163)
{
chk[0] = 1;
}
if ((bt[6] ^ 51) != 117)
{
chk[0] = 1;
}
}
}
That is common xor, using python to find flag.

Flag: dYnaaMic